Category Archives: Cybersecurity

Bypassing Root CA Checks in Android Apps Built with Flutter
Android App Security: In this post, I will explore the topic of bypassing Root Certificate Authority (CA) checks in Android applications developed using the Flutter framework. Although it is important to note that bypassing these security measures is generally not recommended, I aim to provide insights into the technical aspects for educational purposes only. Understanding […]

Talking about Information Security Awareness
Information Security Awareness In the current society, with the rapid development of new-generation information technologies such as artificial intelligence and big data, people’s lives have become more and more convenient and fast. However, when we enjoy technological life, we don’t realize that we have been exposed to dangers such as information fraud, information capture and information […]

How to be a Hacker or a Cybersecurity Expert?
So you want to be a Hacker? Recently I’ve been reading a ton of questions, posts and general discussion about getting into the ‘Information Security’ game, and in my opinion at least it’s typically followed up by a fair amount of misleading information. That might be a little harsh considering I’m sure it’s good intentioned, […]
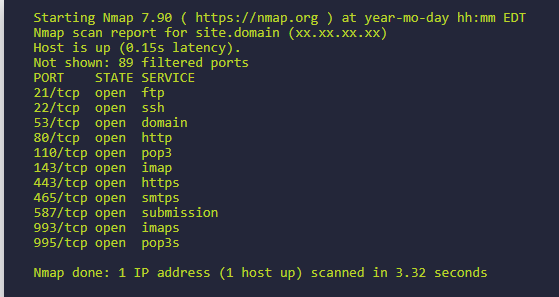
Active Information Gathering with Metasploit-Framework
Using Nmap to perform port scanning Using -sT scanning mode is the default scanning mode of Nmap. The status of the target port is accurately judged through the TCP three-way handshake packet. Since three connections are established, it is extremely easy to be captured by the target firewall. msf> nmap -sT 127.0.0.1 The -sS scan […]
Offensive and Defense Exercise Preparation | How to build an effective corporate security defense system
After the epidemic, work and life gradually returned to normal. For the network security industry, offensive and defensive drills are once again on the agenda. In the new year, how do companies prepare for defense? Let us find the answer from the review and reflection in 2019/20. In 2019/20, offensive and defensive exercises once became […]

How Do Hackers Break Into Websites?
As a company’s operation and maintenance personnel, especially for large and medium-sized enterprises, it is not uncommon for websites and web applications to be attacked by hackers. Web apps and website can be divided into three sections: individual operations, team/company operations, and government operations. The proportion of personal websites is still very large, and most […]
Mimikatz Exploration – WDigest
Mimikatz, to this day, remains the tool of choice when it comes to extracting credentials from lsass on Windows operating systems. Of course this is due to the fact that with each new security control introduced by Microsoft, GentilKiwi always has a way out. If you have ever looked at the effort that goes into […]

Automated Lab: Automate Your Active Directory Security Lab
Building an active directory security lab is not easy, it requires time and resources as well as skills. What if we had an automated way of doing all the hard work? Well, that’s where AutomatedLab! Is convenient! github.com AutomatedLab (abbreviated as AL ) is an automated construction framework for Windows environments developed by Microsoft . You can use it to create labs in […]