Category Archives: Uncategorized
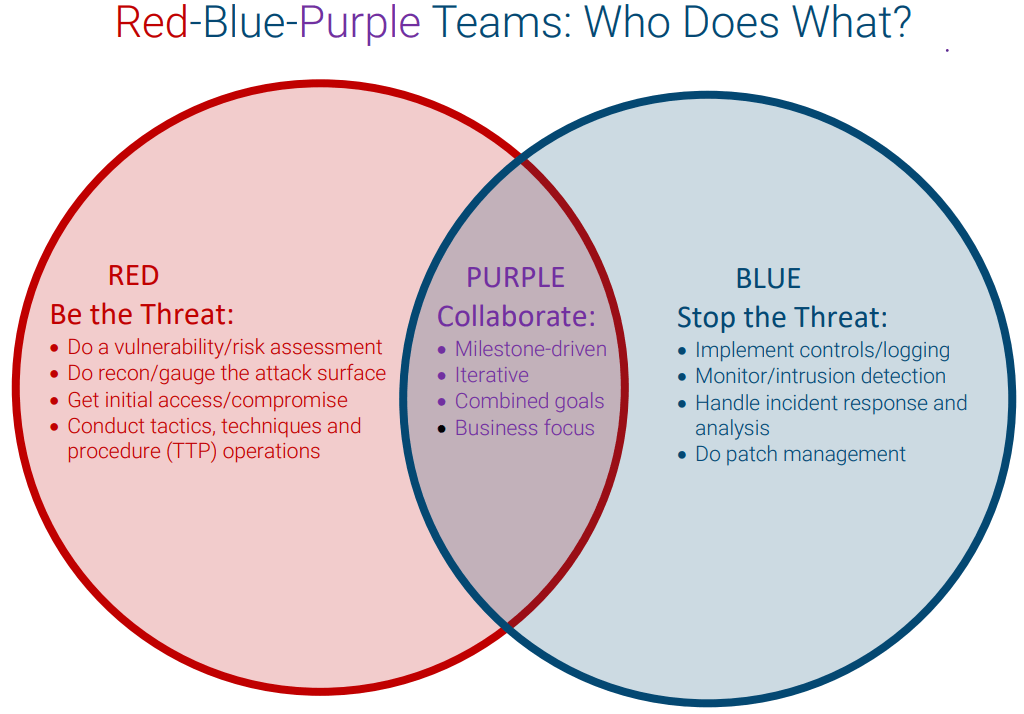
Red Team, Blue Team, and Purple Team: Understanding the Roles in Cybersecurity
, , – Red, Blue, and Purple Teams are terms often used in the context of cybersecurity and information security to describe different roles and approaches in testing and improving the security of an organization’s systems and networks. Here’s an overview of each team and their respective roles: Red Team: Role: The Red Team represents […]
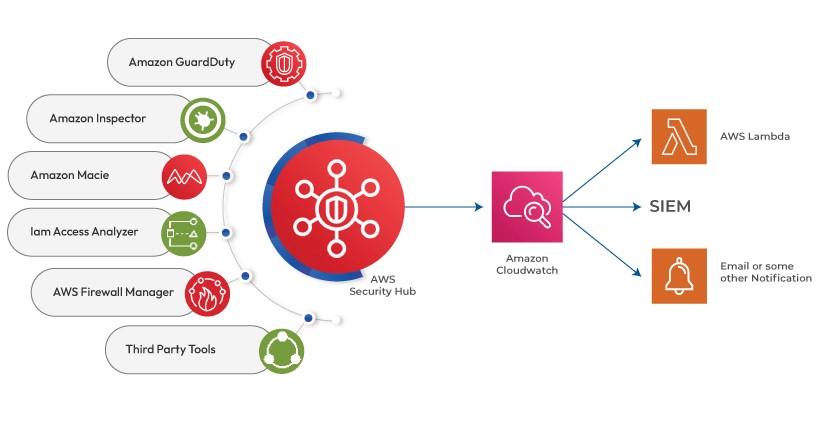
Leveraging AWS IAM Permissions for Complete Cloud Takeover: An Actual Case Study
Part 1 – AWS Security Introduction: In this real-world case study, we delve into the enumeration and strategic utilization of AWS IAM permissions. It is strongly recommended that you familiarize yourself with my prior article explaining the intricacies of IAM permissions, despite its length, as it serves as a foundational prerequisite for comprehending the tactics […]