Red Team, Blue Team, and Purple Team: Understanding the Roles in Cybersecurity
, , –
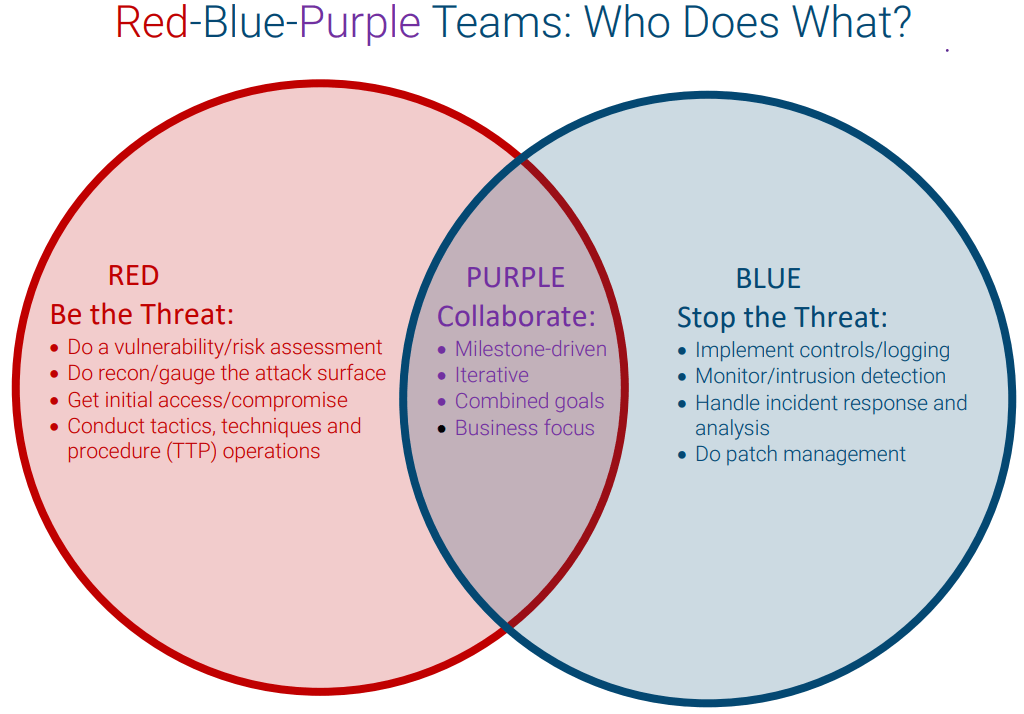
Red, Blue, and Purple Teams are terms often used in the context of cybersecurity and information security to describe different roles and approaches in testing and improving the security of an organization’s systems and networks. Here’s an overview of each team and their respective roles:
- Red Team:
- Role: The Red Team represents the attackers or adversaries. Their primary role is to simulate cyberattacks on an organization’s systems, networks, and infrastructure to identify vulnerabilities and weaknesses.
- Activities:
- Conduct penetration testing to exploit vulnerabilities.
- Use hacking techniques to breach defenses.
- Mimic real-world attack scenarios.
- Test the organization’s incident response capabilities.
- Provide a comprehensive report on findings and recommendations for improvement.
- Goal: To identify weaknesses in the organization’s security posture, which can help the organization proactively improve its defenses and response capabilities.
- Benefits: Red Team exercises help organizations identify vulnerabilities and gaps in their security measures that may not be apparent through traditional security assessments.
- Blue Team:
- Role: The Blue Team represents the organization’s defenders. Their primary role is to protect the organization’s systems, networks, and data from cyber threats and to detect and respond to security incidents.
- Activities:
- Monitor and analyze network traffic and system logs.
- Implement and manage security controls and tools.
- Develop and maintain incident response procedures.
- Investigate and respond to security incidents.
- Continuously assess and improve security measures.
- Goal: To maintain a strong and resilient security posture, detect and respond to threats in real-time, and minimize the impact of security incidents.
- Benefits: Blue Team activities are crucial for day-to-day security operations, threat detection, and incident response, helping organizations defend against cyber threats.
- Purple Team:
- Role: The Purple Team is a collaborative effort that combines elements of both the Red Team and Blue Team. Its role is to improve communication and cooperation between these teams.
- Activities:
- Conduct controlled exercises with Red Team and Blue Team members working together.
- Share information about vulnerabilities, attack techniques, and defensive measures.
- Test and refine incident response procedures in real-time.
- Collaboratively assess and improve security controls.
- Goal: To enhance the overall security posture of the organization by fostering collaboration between offensive (Red) and defensive (Blue) teams.
- Benefits: Purple Team exercises promote a more holistic and coordinated approach to cybersecurity. They ensure that Red and Blue Teams work together to address vulnerabilities and threats effectively.
In summary, Red Teams simulate cyberattacks to uncover vulnerabilities, Blue Teams defend against threats and respond to incidents, and Purple Teams facilitate collaboration between the two to enhance an organization’s overall security posture. These teams play essential roles in proactive security testing, incident response, and continuous improvement in the ever-evolving field of cybersecurity.
#cybersecurity #redteam #redteaming #blueteam #purpleteam #InfoSec #cyberdefense